Meet CPG 235 Requirements
Konverge and Forcepoint assists clients to comply with APRA CPG 235

The Australian Prudential Regulation Authority's (APRA) CPG 235 standard, "Managing Data Risks," aims to strengthen data governance within financial institutions. While crucial, many companies struggle with manual compliance processes that are inefficient, error-prone, and complex.
Konverge offers a leading solution by Forcepoint, that simplifies and automates CPG 235 compliance. Forcepoint's comprehensive platform provides IT security, data security, and compliance services tailored for the financial industry.
Key Challenges of CPG 235
CPG 235 is applicable to all financial entities in Australia offering deposit and insurance products. It mandates effective management of data security risks, not only for compliance but also to protect business reputation and align with global standards like GDPR.
A Comprehensive Solution
Clause 27 of CPG 235 requires a clear understanding of data flow (data lineage) throughout its entire lifecycle. Forcepoint's solution excels by automating data lineage, showcasing the origin, usage, transformation, and destination of data. This comprehensive approach empowers organisations to:
- Establish a unified system of record for all assets.
- Utilise AI for real-time error identification and prevention.
- Generate compliance reports, particularly for sensitive data.
- Track data movement across the entire organisation.
The Importance of Data Lineage
Data lineage provides a visual representation of data movement from ingestion to disposal. It identifies issues related to quality, security, privacy, and governance, enabling swift action and process improvement.
Data Lifecycle and Disposal
To fully meet CPG 235 requirements, Konverge and Forcepoint recommends mapping lineage diagrams for regulated business processes. Their automated data lineage identifies potential security gaps and optimises data handling for both efficiency and compliance.
The Future of Managing Data Risk is here with Forcepoint
Forcepoint provides a holistic data security model to protect, process, understand data risks and act as your reliable custodians of your data.
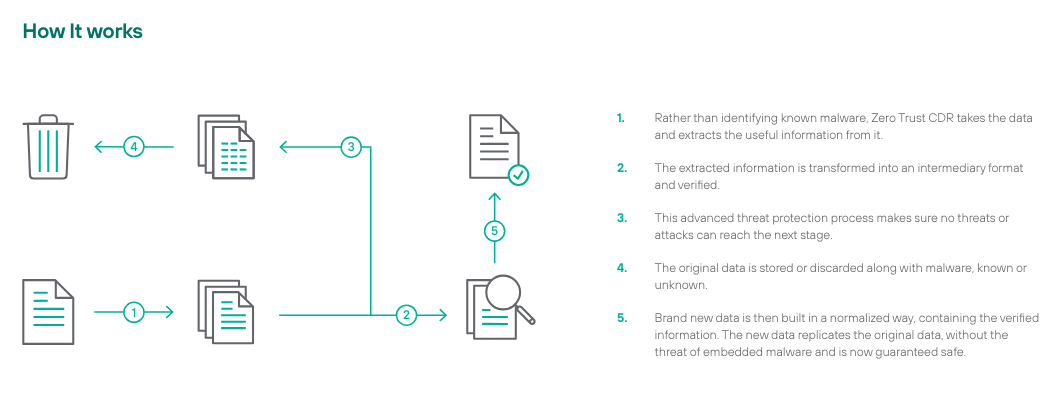
Included in your solution package is Forcepoint's Zero Trust Content Disarm and Reconstruction. It is the only way to mitigate data via steganography, i.e. the hiding of data within image files, whereby malicious actors hide malware and other harmful content to infiltrate the heart of your enterprise.
Fill in the below to download RCDR Brochure
Contact us today to find out how we can assist you with your journey from data loss prevention and privacy to now a duty of care holistic data security.
We can assist you to depict how our solution will affect the following:
Impact Topline
- Protect brand reputation & trust.
- Avoid legal consequences & liabilities.
Improve Data Hygiene
- Understand where it is, who has access.
- Clean up and archive aging data.
- Reduce the threat landscape.
Increase Awareness & Vigilance in Data Security
- Employ tools necessary, Discover, Classify, Monitor & Protect to secure IP and regulated data.
- Spend less and minimise ongoing maintenance of data security.
Meet Compliance & Privacy Requirements driven by Government Regulations
You can rely on Konverge's holistic approach to automate your CPG 235 compliance programs, reducing complexities, costs, risks and ensuring adherence to data regulations. We use Zero-Trust concept that has now evolved in the minds to be at a data level. Data Security Posture Management (DSPM) in the cloud, protecting data and bios in the cloud is important and also a necessity in the current digital landscape.
Fill In below for a personalised demo